
今天突然了解到IPv4中有一个“彩蛋”:Evil bit. 觉得很有意思所以在这里记下来。
首部结构
我们先看一下维基百科 IPv4给出的IPv4首部结构:
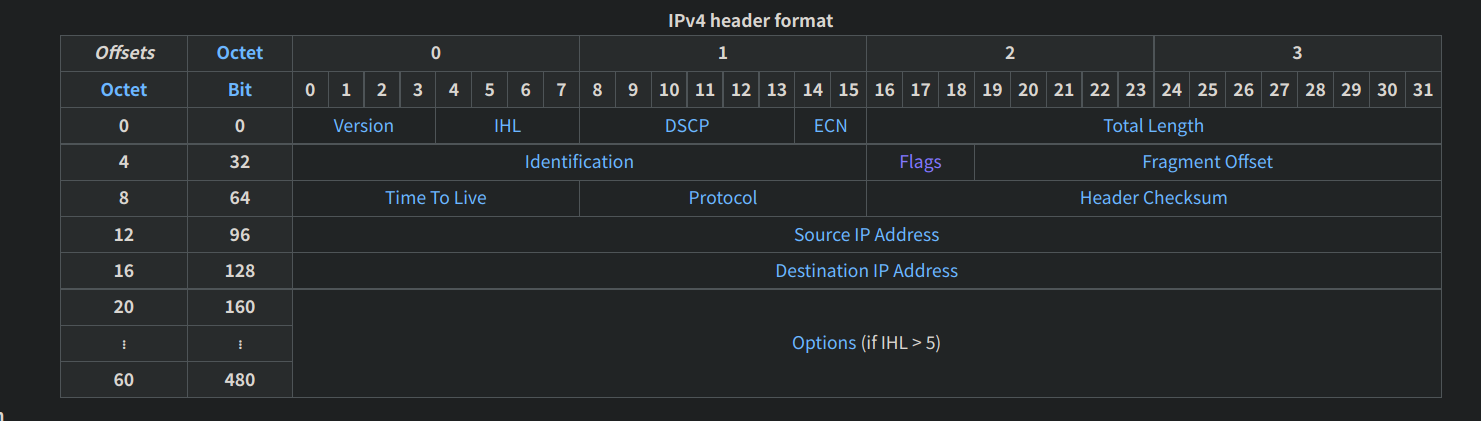
可以看到其中有一个3位的Flags标志,flags的第一位就是我们的Evil bit, 第二位是DF(不分片),第三位是MF(还有分片)。
Evil bit来源
在维基百科 Evil bit中说到了Evil bit来源于RFC 3514, 是一个愚人节的幽默玩笑,用于指出ip数据包是不是有恶意的,因为有了这个字段,所以接收方只需要检查Evil bit就可以知道数据包是否是恶意数据包。
The evil bit is a fictional IPv4 packet header field proposed in RFC 3514, a humorous April Fools' Day RFC from 2003 authored by Steve Bellovin. The RFC recommended that the last remaining unused bit, the “Reserved Bit”^[1]^ in the IPv4 packet header, be used to indicate whether a packet had been sent with malicious intent, thus making computer security engineering an easy problem – simply ignore any messages with the evil bit set and trust the rest.
当然了,都说了是愚人节玩笑了,那怎么可能有用嘛,不过倒是真的有这个字段,就是没啥用,一般博客或者文章也不会提及这个字段是干嘛的。
而在RFC 3514中煞有其事地提到:
Currently-assigned values are defined as follows:
0x0 If the bit is set to 0, the packet has no evil intent. Hosts, network elements, etc., SHOULD assume that the packet is harmless, and SHOULD NOT take any defensive measures. (We note that this part of the spec is already implemented by many common desktop operating systems.)
0x1 If the bit is set to 1, the packet has evil intent. Secure systems SHOULD try to defend themselves against such packets. Insecure systems MAY chose to crash, be penetrated, etc.
后记
除了本文所说到的Evil bit彩蛋之外, 其实有很多IT项目都是有彩蛋的。例如redis的LOLWUT(甚至还能加参数),也有让人离职的Antd圣诞彩蛋(bushi).
- Post title:IPv4首部中的Evil bit
- Post author:QBug
- Create time:2021-08-15 17:44:34
- Post link:https://q-bug4.github.io//articles/2021/08/15/1629020674611.html
- Copyright Notice:All articles in this blog are licensed under BY-NC-SA unless stating additionally.